Types of Consensus Mechanisms – Lotus Crypoos
Blockchain networks rely on consensus mechanisms to validate transactions, secure the ledger, and coordinate participant behavior. Each algorithm balances three core properties—security, scalability, and decentralization—in different ways. Choosing the right consensus mechanism directly impacts a network’s performance, cost, and energy footprint.
Proof of Work (PoW)
Proof of Work is the pioneering consensus protocol that powers Bitcoin and many early blockchains. It requires miners to perform computationally intensive hashing puzzles to propose new blocks. The first miner to solve the puzzle broadcasts the solution, and the network quickly verifies its validity.
- How it works: Miners iterate nonces to find a hash below a dynamically adjusted difficulty target.
- Advantages:
- Strong security backed by economic cost of attacks
- Mature tooling and robust miner networks
- Disadvantages:
- Extremely high energy consumption per transaction
- Limited throughput (5–15 TPS)
- Notable examples: Bitcoin, Litecoin, Ethereum (pre-Merge)
Proof of Stake (PoS)
Proof of Stake shifts block creation from computational work to economic stake. Validators lock up a native token as collateral and are pseudo-randomly selected to propose and attest to blocks. Misbehavior leads to slashing (loss of stake), aligning incentives without massive energy use.
- How it works: Validators stake tokens and get chosen based on stake size and randomness.
- Advantages:
- Orders of magnitude lower energy consumption than PoW
- Higher throughput potential (up to thousands of TPS)
- Disadvantages:
- “Nothing at stake” concerns without robust slashing rules
- Risks of centralization if large holders dominate stake
- Notable examples: Ethereum 2.0, Cardano, Tezos
Delegated Proof of Stake (DPoS)
Delegated Proof of Stake adds a governance layer: token holders vote for a limited set of delegates (or “witnesses”) who secure the network on their behalf. This representative model trades some decentralization for fast, efficient consensus.
- How it works: Stakeholders elect a small committee of delegates who rotate block production.
- Advantages:
- Very high transaction throughput (hundreds to thousands of TPS)
- Lower latency and faster finality
- Disadvantages:
- Greater centralization risk due to small delegate pool
- Voter apathy can concentrate power
- Notable examples: EOS, Tron, Steem
Practical Byzantine Fault Tolerance (PBFT)
Practical Byzantine Fault Tolerance is a voting-based protocol designed for permissioned networks. Nodes exchange signed messages in multiple rounds, ensuring consensus as long as fewer than one-third are malicious or offline.
- How it works: Nodes broadcast proposals and votes in three phases—pre-prepare, prepare, and commit.
- Advantages:
- Instant finality once votes exceed threshold
- Low energy use and high throughput in closed networks
- Disadvantages:
- Communication overhead scales quadratically (n²)
- Requires known, permissioned participants
- Notable examples: Hyperledger Fabric, Tendermint (in Cosmos SDK)
Proof of Authority (PoA)
Proof of Authority entrusts a set of pre-approved validators—identified and audited entities—to create blocks. Identity and reputation serve as collateral instead of tokens or compute power.
- How it works: A fixed group of authorities takes turns producing blocks in a round-robin or BFT-style process.
- Advantages:
- Extremely efficient and low-latency finality
- Predictable performance in enterprise settings
- Disadvantages:
- Minimal decentralization makes it less censorship-resistant
- Trust relies on validator identities
- Notable examples: Ethereum’s Kovan testnet, VeChain, POA Network.
Proof of Elapsed Time (PoET)
Proof of Elapsed Time (PoET) relies on a secure hardware enclave to assign each node a randomly generated wait time. The first node whose timer expires earns the right to propose the next block, creating an energy‐light, fair lottery for block creation2.
- How it works:
- Each node runs trusted code in a TEE (such as Intel SGX) to generate a random wait time.
- Nodes pause (“sleep”) until their timer expires, avoiding wasteful computations.
- The node with the shortest elapsed time broadcasts its block.
- Peers verify the block and TEE-provided attestations before adding it to the chain.
- Advantages:
- Minimal energy usage compared to PoW or even PoS.
- Equal opportunity for all participants via randomized selection.
- Scales well in permissioned environments with high throughput needs.
- Disadvantages:
- Requires specialized trusted hardware, increasing setup complexity.
- Primarily suited for permissioned blockchains, limiting open participation.
- Dependence on hardware vendors can introduce centralization risks.
- Notable examples: Hyperledger Sawtooth, various enterprise PoET prototypes.
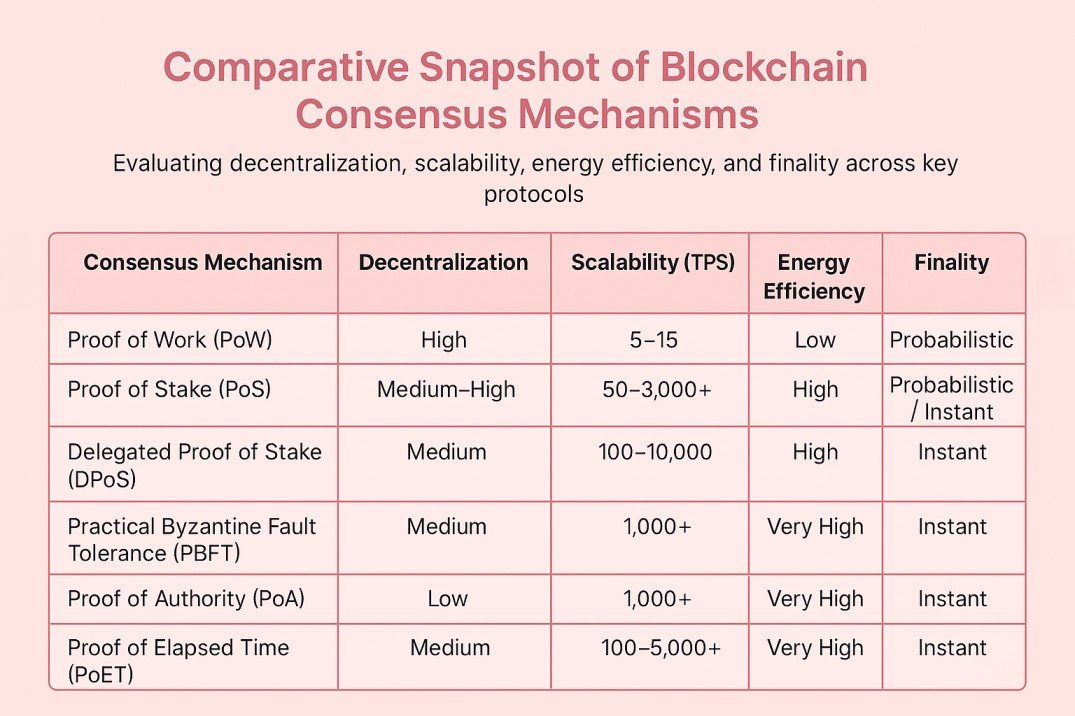
| Consensus Mechanism | Decentralization | Scalability (TPS) | Energy Efficiency | Finality |
|---|---|---|---|---|
| Proof of Work (PoW) | High | 5–15 | Low | Probabilistic |
| Proof of Stake (PoS) | Medium–High | 50–3,000+ | High | Probabilistic / Instant |
| Delegated Proof of Stake (DPoS) | Medium | 100–10,000 | High | Instant |
| Practical Byzantine Fault Tolerance (PBFT) | Low–Medium | 1,000+ | Very High | Instant |
| Proof of Authority (PoA) | Low | 1,000+ | Very High | Instant |
| Proof of Elapsed Time (PoET) | Medium | 100–5,000+ | Very High | Instant |
Conclusion-
Selecting a consensus mechanism involves trade-offs across security, performance, and decentralization. Proof of Work remains the gold standard for trustless, censorship-resistant networks, while Proof of Stake and its variants offer greener, faster alternatives. For private or consortium chains, PBFT and PoA deliver instant finality at the expense of open participation.
Read Also-