Blog
Tether Whitepaper and Overview
Tether (USDT) is the world’s most widely used stablecoin, designed to maintain a 1:1 peg with fiat currencies like the US dollar. Here is your Tether Whitepaper. Get your Tether Whitepaper here Key Facts from Tether Whitepaper Launched in 2014, Tether was created to enable digital transactions using traditional currencies without volatility. USDT is pegged […]
What Is Sybil Resistance in Blockchain? Examples and Preventions
A Sybil attack occurs when a malicious actor floods a blockchain network with multiple fake identities (nodes) to gain disproportionate influence over consensus or resource allocation. By masquerading as numerous distinct participants, the attacker can manipulate voting processes, censor transactions, or compromise network security. The term “Sybil” traces back to a 1973 novel about a […]
ZK-SNARKs vs ZK-STARKs: Ultimate Comparison Guide
Zero-knowledge proofs let you validate computations without revealing underlying data. ZK-SNARKs and ZK-STARKs both deliver succinct proofs, but they diverge on trust assumptions, transparency, quantum resistance, proof sizes, and computational trade-offs. This post unpacks definitions, core differences, practical use cases, and future directions to help you choose the right technology for your project. So dive […]
The DAO Attack – Reentrancy Vulnerability
The DAO attack on Ethereum in 2016 stands as the most famous reentrancy exploit in smart contract history. By recursively withdrawing funds before its internal state could update, an attacker drained about 3.6 million ETH in a matter of hours. This blog post unpacks how reentrancy works, walks through The DAO vulnerability, and outlines prevention […]
How to do Fundamental Analysis of Cryptocurrencies?
Investing in cryptocurrencies without understanding their underlying value is like sailing in open waters without a compass. Fundamental analysis equips you with the tools to evaluate a project’s long-term viability by examining its technology, team, tokenomics, and on-chain metrics, rather than chasing short-term price swings. Understand Project Fundamentals Start by diving into the project’s core […]
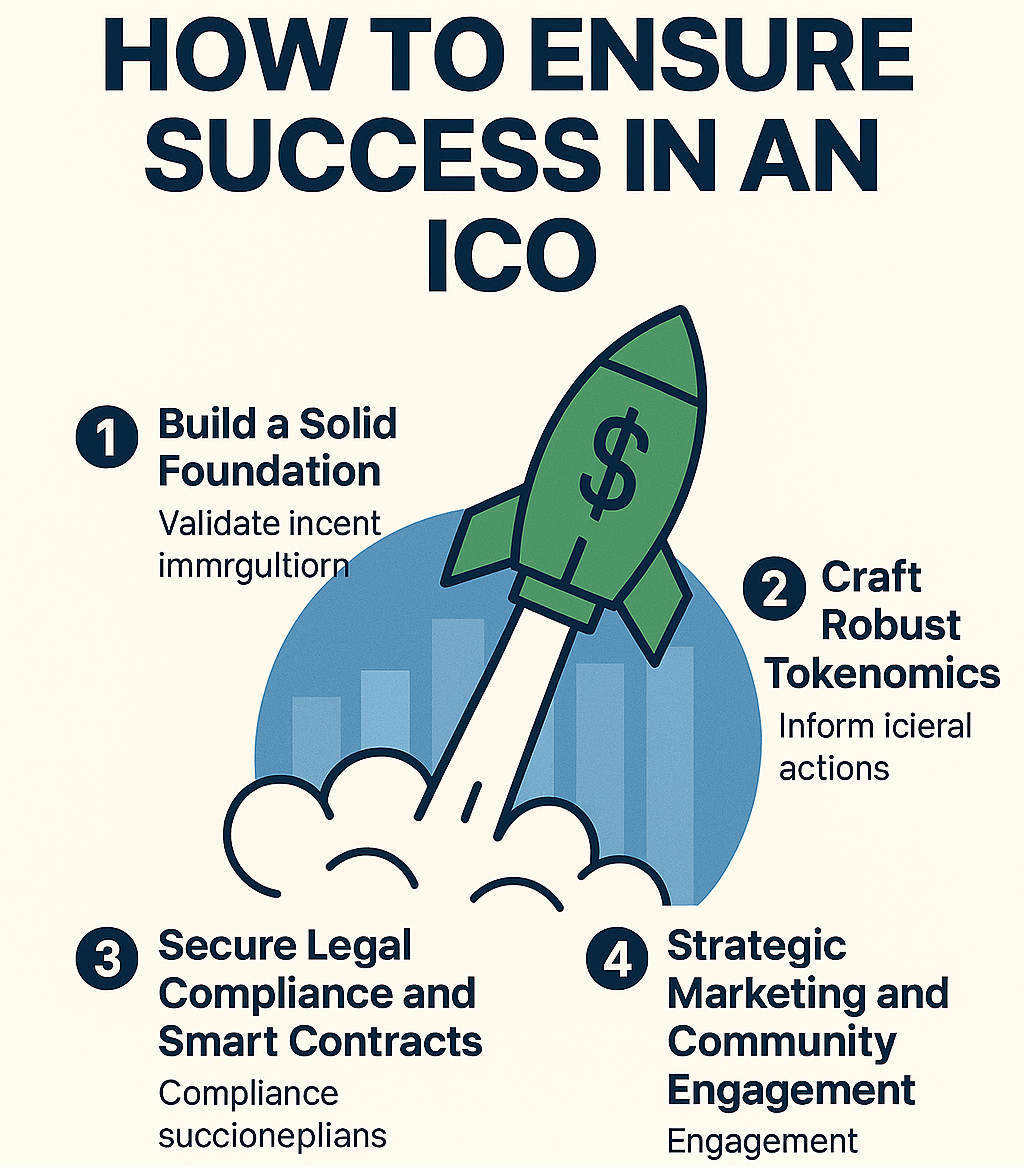
How to Ensure Success in ICO?
Launching an Initial Coin Offering (ICO) in today’s competitive crypto landscape demands much more than minting tokens—it requires a holistic strategy that spans product validation, tokenomics, legal compliance, marketing, and post-ICO growth. Follow these seven key steps to ensure success in ICO and maximize your chances of a breakthrough sale. Build a Solid Foundation Before […]
WazirX Scam – India’s One of the Biggest Crypto Controversies
In July 2024, India’s largest crypto exchange, WazirX, suffered a massive breach that shook the nation’s burgeoning digital asset ecosystem. Over $230 million vanished almost overnight, leaving tens of thousands of retail investors in limbo and prompting fierce debates over security, accountability, and the need for clearer crypto regulations. Here are insights into the WazirX […]
What is Overflow and Underflow in Solidity? Methods to Prevent It
Smart contracts execute financial logic directly on the blockchain. A tiny arithmetic mistake can unlock millions in unintended Ether transfers. Two of the most infamous pitfalls are integer overflow and underflow. Understanding how they work—and how to guard against them—is essential for any Solidity developer. Understanding Overflow and Underflow in Solidity Solidity uses fixed‐size unsigned […]
Top Cryptocurrency ETFs – All You Need to Know
Cryptocurrency exchange-traded funds (ETFs) have exploded in popularity since the SEC’s landmark approval of spot Bitcoin and Ethereum ETFs in early 2024. These funds blend the ease and regulation of traditional finance with direct exposure to digital assets, opening the door for investors who prefer to stay within familiar brokerage accounts. Top Bitcoin ETFs iShares […]
Top 10 Meme Coins in 2025
Meme coins have gone from internet jokes to headline-grabbing assets, powered by viral communities, celebrity shout-outs, and unconventional tokenomics. Here’s our roundup of the top 10 meme coins you should know in 2025, along with what makes each one stand out. Dogecoin (DOGE) Dogecoin remains the original meme coin and still commands one of the […]